Polymarket users complain of mysterious Google login wallet attacks
According to an old version of Polymarket documents, it uses the Magic software development kit (SDK) from Magic Labs to allow for passwordless, seedless logins. This is why users can log into the app without needing to download a standard Web3 wallet
Some users of the Polymarket prediction market app are complaining that their wallets were mysteriously drained after they logged in via their Google accounts.
After making deposits, users found that their wallets were wiped out, leaving a balance of zero. The attacks have not occurred against users that relied on wallet browser extensions such as MetaMask or Trustwallet.
The first victim identified himself by the Discord username, “HHeego,” and claimed to be the owner of a Polymarket account whose address ends in C3d4.
HHeego claimed that he deposited $1,085.80 in USD Coin from Binance to Polymarket on Aug. 5. However, after hours of waiting, the deposit did not show up in his account within the Polymarket app.
Believing something was wrong with his account, HHeego joined the Polymarket Discord server in an attempt to get help. He found that many other users were having similar problems, and it seemed to be connected to a user interface issue. This made him feel relieved, so he stopped worrying about it.
Later that day, the deposit appeared on the user interface. However, he stated that it “vanished almost as quickly as it had come.” In fact, he claimed that his entire USDC balance of $1,188.72 disappeared. This balance included $102.92 that had been in the account before the deposit was made, as well as the deposit itself.
Strangely, HHeego’s $2,000 worth of open trades remained untouched.
HHeego seeks help from Polymarket
HHeego inspected his account history using the Polygonscan block explorer and found that his USDC balance had been sent to an account labeled “Fake_Phishing399064.”
He then submitted a ticket to customer support. When the customer support agent heard the user’s story, he expressed incredulity. “Haven’t you withdrawn that amount?” he asked. “No i havent,” the user replied. “Are you sure it wasn’t you then?” the agent asked. “I am 100% sure,” the user replied.
The agent asked HHeego if “your PK got leaked or you got phished somehow.” The user, who claims to be a newcomer to the crypto world, told that he did not at first understand what the agent meant by a “PK leak.” HHeego stated that he has never used a browser extension wallet and has only ever used a Google login to access Polymarket.
After asking a few more questions, the agent told him that the team was investigating the anomaly and would contact him when they discovered more information.
Another $4,000 gets swiped
Believing that the wallet drain was some kind of “glitch” that would eventually be worked out, HHeego deposited an additional $4,111.31 on Aug. 11. As before, the “fake phishing” account drained all of the funds, bringing the user’s total losses to $5,197.11.
At this point, the user became convinced that his Polymarket account was hacked. He closed all of his trades, amounting to nearly $1,000 in funds, and withdrew his balance to his Binance account. The proceeds from these trades were not touched by the attacker, and the withdrawal was successful.
How Google logins work on Polymarket
According to an old version of Polymarket documents, it uses the Magic software development kit (SDK) from Magic Labs to allow for passwordless, seedless logins. This is why users can log into the app without needing to download a standard Web3 wallet such as Metamask or Coinbase Wallet.
The Magic documents go into greater detail as to how this system works. According to it, users generate a “user master key” when they first sign up for an integrated service such as Polymarket. This master key can be used to decrypt another encrypted key stored on the user's device.
The master key is stored on an Amazon Web Services (AWS) hardware security module. This means that an attacker should not be able to initiate a transaction on Polymarket without first authenticating with the AWS server.
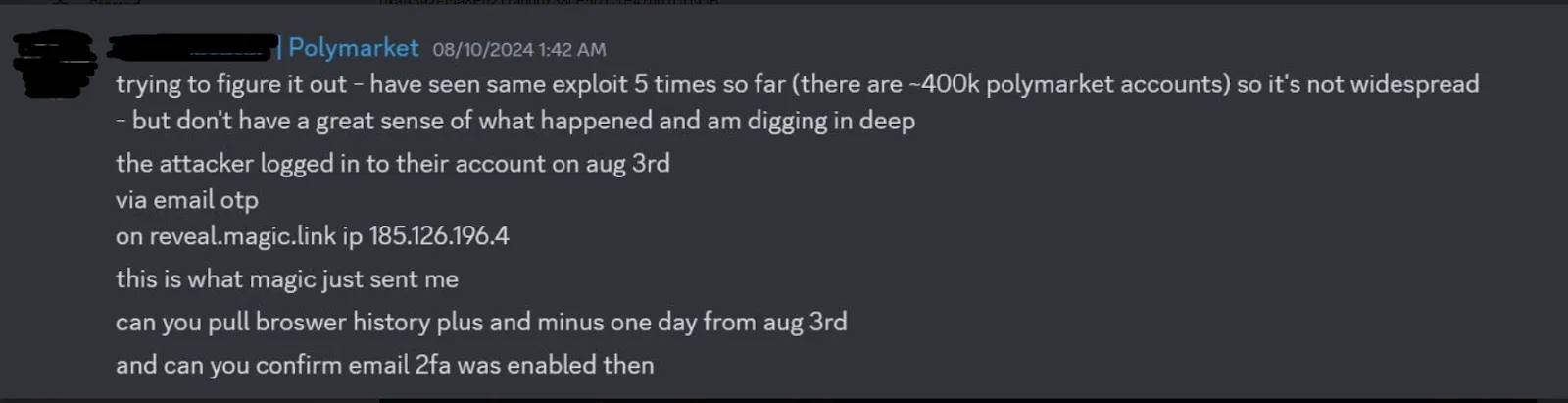
In the case of a Google login, an attacker should not be able to authenticate without gaining access to the user's Google account. Both victims claimed that they saw no evidence of anyone having gained access to their Google accounts.
The message to Cryptomaniac cited above stated that the attacker used “Email OTP [one time password]” to authenticate with the server. This implies that the attacker must have gained access to the victims’ email accounts. However, both victims claimed they never used an email address to access the platform.
None of the victims used wallet extensions to access the platform. So it appears that the exploit may only work against newer login method types such as Oauth or email OTP.
According to reports from victims, Polymarket has cgit commit -m "Update"laimed that the attacks are only occurring against a few users and are not widespread.